A vulnerability refers to weaknesses or flaws in an IT network that attackers can exploit to gain unauthorized access, perform malicious actions, or compromise the security of an organization’s data and network. Cybercriminals are constantly on the lookout for vulnerabilities to exploit, using them as a means to launch attacks such as data breaches, malware infections, or denial of service attacks. This is where Pen testing services come into play, identifying and addressing these weaknesses before they become a real threat.
Vulnerability Management System and Pen Testing Services
Get startedVULNERABILITIES ARE THE ACHILLES HEEL OF YOUR IT INFRASTRUCTURE- Discover vulnerabilities before hackers can exploit them
What is a vulnerability?
Vulnerability Management
Implementing a robust vulnerability management strategy is crucial for identifying, evaluating, and addressing these weaknesses before they can be exploited by malicious actors. This ongoing process includes regular VAPT testing and vulnerability assessments to discover potential threats and mitigate risks effectively.
The Importance of a Vulnerability Management System
A comprehensive vulnerability management system is essential for maintaining the security of an organization’s IT infrastructure. Vulnerability management systems provide automated tools to detect and remediate vulnerabilities, ensuring that the network remains secure against potential threats. Integrating Pen testing services and VAPT testing into your vulnerability management strategy enhances your ability to detect and address these issues proactively.
60% of data breaches are caused by unpatched vulnerabilities.
70% of applications contain at least one vulnerability after 5 years in production.
84% of companies have high-risk vulnerabilities, half of which could be removed with a simple software update.
What causes it?
When it comes to vulnerabilities, it is crucial to recognize and address the root causes of them to effectively safeguard your valuable digital assets and maintain a strong security posture. Implementing a vulnerability management program, which includes regular Pen testing services and VAPT testing, is essential in identifying and mitigating potential threats. A comprehensive vulnerability management system ensures that all aspects of your network are continuously monitored and assessed for weaknesses. Regular vulnerability assessments help in detecting and addressing security gaps before they can be exploited by malicious actors. A few of those root causes are:
Design flaws
Programming errors
Configuration issues
Outdated software
Human errors
Third-party components
What Happens When You Leave a Vulnerability Uncovered?
When vulnerabilities are left unaddressed, attackers can gain unauthorized access, steal sensitive data, or disrupt your business operations. This can lead to:
Financial losses
Damage to reputation
Legal liabilities
Loss of customer trust
Business interruption
By integrating a comprehensive vulnerability management strategy, including Pen testing services and VAPT testing, you can safeguard your organization against potential breaches and maintain the integrity of your operations.
Pathway’s Vulnerability Management services provide a comprehensive solution to protect your business from ever-evolving cyber threats. Our dedicated team of security experts works round-the-clock to detect, assess, and prioritize vulnerabilities within your systems, ensuring a proactive approach to safeguarding your valuable data and assets. By leveraging our extensive experience and state-of-the-art tools, including VAPT testing, we empower your organization to stay one step ahead of potential security breaches and maintain business continuity.
Our structured approach to Vulnerability Management, which incorporates both Pen testing services and VAPT testing, detects, assesses, and addresses vulnerabilities to bolster your security posture and mitigate risks. It helps you stay one step ahead of potential vulnerabilities, safeguarding your business from potential disruptions and data breaches.
Additional Focus on Vulnerability Assessment
In addition to ongoing vulnerability management, conducting periodic vulnerability assessments provides deeper insights into potential security gaps. These assessments identify hidden risks across networks, applications, and devices, allowing organizations to prioritize remediation efforts effectively. Pairing vulnerability assessments with a strong vulnerability management system ensures both proactive and reactive defense mechanisms are in place to minimize exposure to cyber threats.
Comprehensive VAPT Testing Approach
VAPT testing combines vulnerability assessment with penetration testing to provide a complete view of your security landscape. While vulnerability assessments identify weaknesses, Pen testing services attempt to exploit them, offering a real-world view of potential attack scenarios. This layered approach strengthens your vulnerability management strategy by ensuring all discovered vulnerabilities are not only documented but also tested for exploitability and business impact.
What We Offer
Our Vulnerability Management service is powered by industry-leading Vulnerability Assessment and Penetration Testing (VAPT) and Patch Management methodologies, which strengthen your infrastructure against the cyber risks of today and tomorrow.
| Vulnerability Assessment (VA) | Penetration Testing (PT) | Patch Management | |
| Focus | FIND
Identifies, quantifies, and prioritizes the vulnerabilities in your IT system using automated scanning tools. |
EXPLOITS
Simulates real-world cyberattacks to assess the effectiveness of your organization’s security measures. |
MITIGATE
Remediates vulnerabilities by applying patches, updates, and configuration changes to reduce exposure and risk. |
| Result | Lists all vulnerabilities and categorizes them based on their severity | Evaluates the potential impact of a breach by exploiting discovered vulnerabilities and identifies areas where improvements are needed. | Tracks and reports on vulnerability remediation progress, ensuring security measures are up-to-date and effective. |
| Value | The findings of VA serve as the base for PT. | The findings of PT are helpful for the remediation process later on | The findings ensures the security measures are up-to-date and effective. |
| Process | Automated testing | Automated and manual testing | Patch management tools, manual updates, and configuration changes. |
| Frequency | Done frequently | Done on demand | Continuous monitoring and periodic updates |
With Pathway’s Vulnerability Management service, rest assured that our team of cybersecurity professionals is diligently safeguarding your organization from cyber threats. Our focus on proactive, comprehensive, and tailored solutions helps protect your valuable assets from cyber threats while maintaining a subtle and supportive approach. Trust in Pathway for a dependable security partnership.
Perks of Vulnerability Management
Enhance Security with VAPT
At Pathway, we understand that a single layer of security is not enough. That’s why our approach combines VAPT testing, vulnerability assessment, and Pen testing services to deliver a multi-layered defense. These practices allow us to identify both internal and external threats, ensuring that no weakness goes unnoticed.
The Role of a Vulnerability Management System
Implementing a vulnerability management system enables continuous monitoring, detection, and remediation of threats across your IT infrastructure. Pathway integrates this system into your security strategy, ensuring a structured approach to vulnerability identification and risk reduction. Combined with VAPT testing and vulnerability assessment, it provides a strong foundation for long-term cybersecurity resilience
Tailored Pen Testing Services for Your Business
Every organization faces unique challenges. Pathway’s Pen testing services are designed to simulate real-world attacks, providing actionable insights into potential exploits. When paired with our vulnerability management and vulnerability management system, these tests help you prioritize and remediate threats quickly and effectively.
Our Technology Partners for Advanced Cybersecurity
Pathway uses a variety of vetted commercial software platforms and tools to deliver the best security services.


Microsoft

Tenable

FortiNet

Rapid7

Kaseya

Elastic Software

RapidFire

Zabbix

KnowBe4

BitDefender

Duo

ESET

Ridge Security

Sprinto

Okta

Veriato

Proofpoint

OutThink.io
Why Pathway
Expertise and experience
Pathway brings 25+ years of knowledge and experience with seasoned professionals who have successfully helped numerous businesses identify, manage, and mitigate cyber risks. Our team’s expertise in vulnerability management, including Pen testing services, ensures that your organization receives proactive and effective security measures.
Tailored solutions
Pathway customizes its VAPT testing services to align with your unique business requirements, delivering tailored and effective security solutions.
Comprehensive and proactive
Pathway’s comprehensive security services provide an all-encompassing approach to your security needs, while our proactive measures help you stay ahead of cyber threats, minimizing risks and preventing breaches. By continuously updating our vulnerability management system and incorporating VAPT Testing, we ensure that your defenses are robust and adaptive.
24/7 dedicated support
Pathway provides round-the-clock support from a team of seasoned security professionals committed to protecting your organization. Our experts monitor your vulnerability management system, ensuring rapid response and mitigation of emerging threats through regular Pen testing services and other advanced methodologies.
SMB-friendly
Cybersecurity is essential for a business, and Pathway Communications believes in making this essential service accessible for businesses of all sizes. That’s why we offer tailored security solutions that fit the needs and budgets of mid-sized and smaller organizations. Our scalable vulnerability management services, including VAPT Testing, ensure that SMBs can achieve enterprise-level security without compromising on quality.
Why choose us?
Fully-equipped, world-class security operations center
Pathway Communications operates a world-class Security Operations Center (SOC) in Markham with experienced security professionals dedicated to protecting your business. Our SOC is equipped with state-of-the-art technology, advanced threat detection and response tools, and a team of elite analysts working 24/7 to monitor your systems and respond to potential threats.
24/7 vigilance against threats
Threats can emerge at any time, day or night. That’s why Pathway offers round-the-clock Managed Detection and Response (MDR), which combines continuous monitoring of all assets, accurate alerts, detection, and rapid response to cyber security events. This ensures your IT infrastructure and applications are properly configured, hardened, and protected with the help of our world-class Security Operations Centre (SOC), which monitors, detects, and responds 24/7.
24/7 access to SOC Cyber Analysts and Elite Threat Hunters
Pathway offers 24/7 access to our team of SOC Cyber Analysts and Elite Threat Hunters so that you can turn to us for help with any cybersecurity issue at any time. This helps to reduce the impact of cyber incidents and minimize downtime, ultimately saving you time and money. Additionally, the peace of mind that comes with knowing that expert support is always available can help you to feel more secure and confident in your cybersecurity posture.
Easy access to reports and records
Pathway’s security systems store your data for reporting and analysis and provide you with access to reports, cases, dashboards, and event updates via a web portal or scheduled batches. You can easily view and analyze your data offline to make informed decisions about your cybersecurity.
Customization
Pathway offers a complete range of security services with budgets of any size. These include packages of bundled services or individual (“a-la-carte”) services which cater to the specific needs of our clients.
Certified experts
Pathway’s team of experienced professionals has expertise in cybersecurity, including risk management, threat analysis, incident response, and compliance. They have a wide range of skills and technical certifications for proactive monitoring and support to your business.
- Certified Information Systems Security Professional (CISSP)
- Certified Cloud Security Professional (CCSP)
- Certified Information Systems Auditor (CISA)
- Cisco Certified Internet Engineer (CCIE) – security and routing
- Unix System Administrators
- Microsoft Certified Solutions Expert (MCSE)
- Microsoft Certified: Azure Solutions Architect (MCASA)
What are Pen Testing Services and why are they important?
Pen Testing Services are security assessments that simulate real cyberattacks to find weaknesses in your systems before hackers do. They help organizations identify security gaps, strengthen defenses, and meet compliance requirements, ensuring that data and critical systems remain protected.
How do Pen Testing Services work?
Pen Testing Services work by using ethical hackers to test applications, networks, and systems for vulnerabilities. They mimic real-world attack methods to expose weaknesses, then provide a detailed report with risks, impact, and recommended fixes. This helps businesses improve security proactively.
What is a Vulnerability Assessment?
A Vulnerability Assessment is a process that scans your systems to identify potential weaknesses, misconfigurations, or outdated software that attackers could exploit. It provides a prioritized list of issues so businesses can fix them before they turn into serious security risks.
How does Vulnerability Management differ from Vulnerability Assessment?
Vulnerability Assessment identifies security flaws at a point in time, while Vulnerability Management is an ongoing process. A Vulnerability Management system continuously detects, prioritizes, and fixes vulnerabilities, ensuring long-term protection against cyber threats.
Why is a Vulnerability Management System necessary?
A Vulnerability Management System is necessary to automate the detection and patching of security gaps across your IT environment. It helps organizations stay ahead of new threats, comply with regulations, and reduce the risk of data breaches by ensuring timely fixes.
What is VAPT Testing?
VAPT Testing (Vulnerability Assessment and Penetration Testing) combines two approaches: scanning systems for vulnerabilities and actively exploiting them like a hacker would. This method provides a complete view of security risks and practical recommendations for improving defenses.
How often should businesses perform VAPT Testing?
Businesses should perform VAPT Testing at least once or twice a year, or whenever major changes occur, such as software updates, infrastructure upgrades, or compliance requirements. Regular testing ensures continuous protection against evolving cyber threats.
How to choose the right Pen Testing Services provider?
To choose the right Pen Testing Services provider, look for certifications (like CREST or OSCP), proven experience, clear reporting practices, and post-test support. Ensure the provider tailors testing to your business needs and complies with industry standards.
Can small businesses benefit from Vulnerability Management?
Yes, small businesses can greatly benefit from Vulnerability Management. Even smaller networks and applications are frequent targets of cyberattacks. A proper vulnerability management system helps protect sensitive data, reduce risks, and build customer trust without heavy costs.
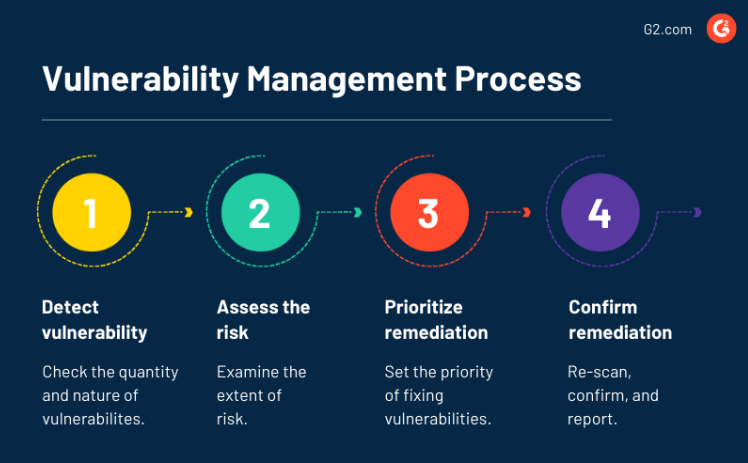
How to implement an effective Vulnerability Management System?
To implement an effective Vulnerability Management System:
- Scan your environment regularly.
- Prioritize vulnerabilities by severity.
- Patch or fix issues quickly.
- Monitor compliance requirements.
- Repeat the cycle for continuous security.

